How To Use RemoteIoT Behind Firewall On Mac Without Breaking A Sweat
Alright folks, let’s cut straight to the chase. If you're reading this, chances are you're scratching your head wondering how to use RemoteIoT behind a firewall on a Mac without pulling your hair out. Don’t worry—you're in the right place. Today, we’ll dive deep into the nitty-gritty of making RemoteIoT work seamlessly even when you're stuck behind a corporate or home firewall. So, buckle up and let’s get started!
Now, before we jump into the technical stuff, it’s important to understand what exactly RemoteIoT is and why it matters. RemoteIoT is essentially a tool designed to help you connect devices and manage them remotely. Whether you're monitoring sensors, controlling smart home gadgets, or managing industrial equipment, RemoteIoT has got your back. But here’s the kicker: firewalls can sometimes get in the way. That’s where our guide comes in—to show you how to bypass those pesky firewalls without breaking any rules.
By the end of this article, you’ll have a crystal-clear understanding of how to set up RemoteIoT on your Mac, navigate through firewall restrictions, and ensure everything runs smoothly. Whether you're a tech enthusiast or just someone trying to get things done, this guide is here to help. So, let’s not waste any more time—here’s the lowdown on how to use RemoteIoT behind a firewall on your Mac!
Read also:Unlocking The World Of Entertainment Your Ultimate Guide To Vegamovies4k
Table of Contents
- Understanding RemoteIoT and Its Importance
- Firewall Challenges When Using RemoteIoT
- Setting Up RemoteIoT on Your Mac
- How to Bypass Firewall Restrictions
- The Role of Port Forwarding
- Using VPNs to Access RemoteIoT
- Ensuring Security While Bypassing Firewalls
- Common Issues and Troubleshooting Tips
- Best Practices for Using RemoteIoT Behind a Firewall
- Wrapping It All Up
Understanding RemoteIoT and Its Importance
So, what exactly is RemoteIoT? Simply put, it’s a powerful platform that allows you to connect, monitor, and control IoT devices remotely. Imagine being able to adjust the temperature of your smart thermostat from miles away or keeping an eye on your security cameras while you're at work. That’s the magic of RemoteIoT. But why is it so important?
In today’s hyper-connected world, IoT devices are everywhere—from our homes to offices and even industrial settings. However, managing these devices can be a challenge, especially if you're not physically present. This is where RemoteIoT steps in, providing a solution that’s both efficient and user-friendly. By enabling remote access, it saves time, reduces costs, and enhances productivity.
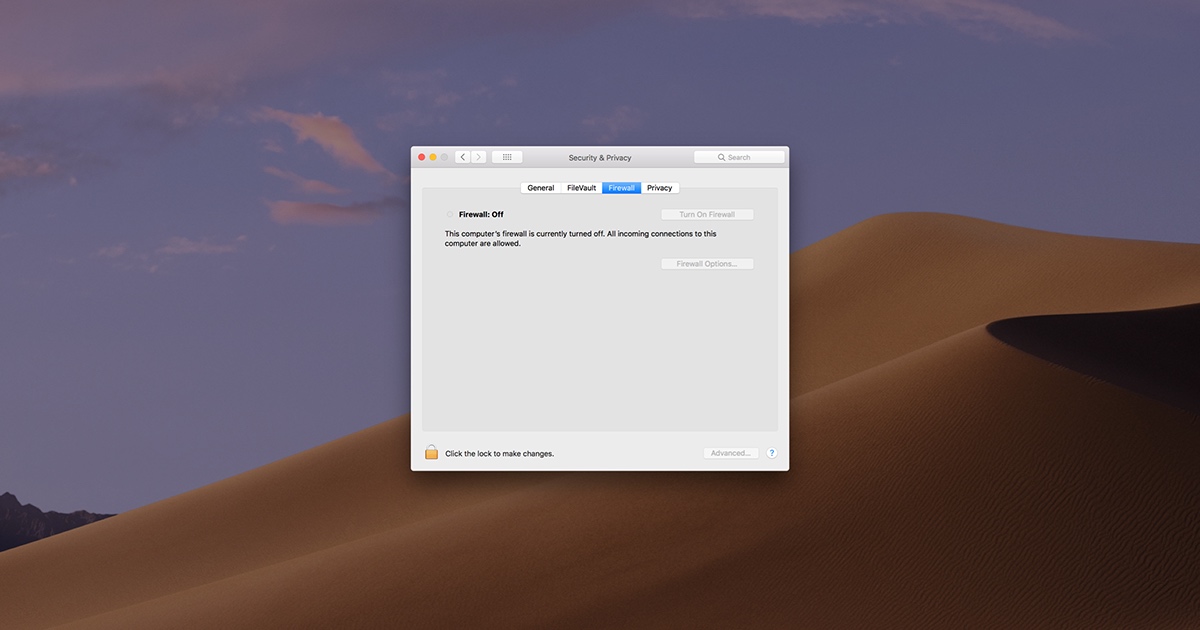
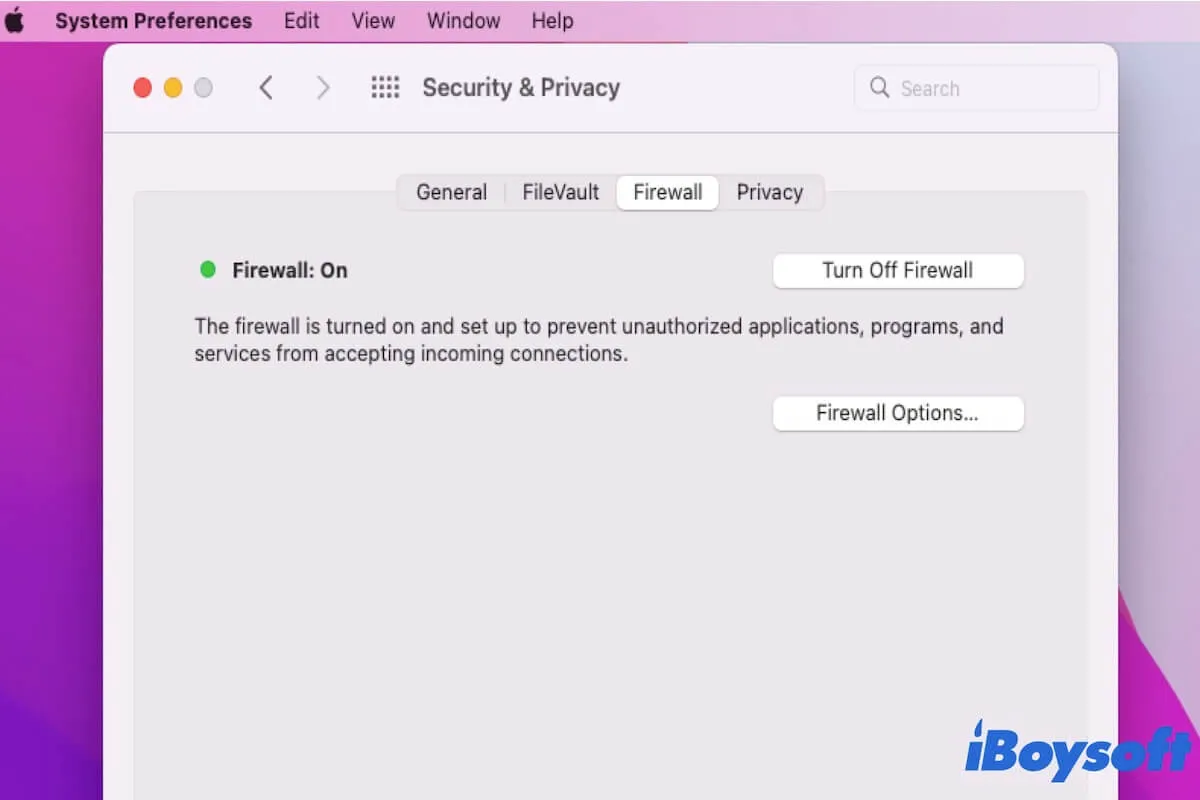
But here’s the thing: firewalls can sometimes make things complicated. Firewalls are designed to protect your network from unauthorized access, but they can also block legitimate connections. That’s why learning how to use RemoteIoT behind a firewall is crucial for anyone looking to maximize its potential.
Firewall Challenges When Using RemoteIoT
Now, let’s talk about the elephant in the room—firewalls. Firewalls are great for security, but they can be a real pain when you’re trying to use tools like RemoteIoT. Here are some common challenges you might face:
- Blocked Ports: Firewalls often block certain ports that RemoteIoT uses to establish connections.
- IP Restrictions: Some firewalls restrict access based on IP addresses, making it difficult to connect from outside the network.
- Encryption Issues: If your firewall isn’t configured properly, it might interfere with the encrypted data RemoteIoT sends and receives.
- Performance Bottlenecks: Firewalls can sometimes slow down your connection, affecting the overall performance of RemoteIoT.
These challenges might sound daunting, but don’t worry—we’ve got solutions for each one. Keep reading to find out how to overcome them!
Why Firewalls Are Necessary
Before we dive into the solutions, it’s worth noting why firewalls are important. Firewalls act as a barrier between your network and the outside world, protecting you from cyber threats, hackers, and unauthorized access. While they might seem like a nuisance at times, they play a vital role in keeping your data safe. The key is finding a balance between security and functionality.
Read also:Vegamoves Revolutionizing The Way We Move And Groove
Setting Up RemoteIoT on Your Mac
Alright, let’s get our hands dirty and start setting up RemoteIoT on your Mac. Here’s a step-by-step guide to help you get started:
- Download the Software: Head over to the official RemoteIoT website and download the latest version compatible with macOS.
- Install the Application: Once the download is complete, open the installer and follow the on-screen instructions to install the software.
- Create an Account: If you haven’t already, create an account on RemoteIoT. This will allow you to access your devices remotely from anywhere.
- Connect Your Devices: Add your IoT devices to the platform by following the setup wizard. Make sure they’re properly configured and connected to your network.
- Test the Connection: Before moving on, test the connection to ensure everything is working as expected.
With these steps, you should have RemoteIoT up and running on your Mac in no time. But what happens when you’re behind a firewall? Let’s find out!
How to Bypass Firewall Restrictions
Bypassing firewall restrictions might sound tricky, but it’s actually quite straightforward. Here are a few methods you can try:
Method 1: Configure Firewall Rules
If you have administrative access to the firewall, you can configure it to allow RemoteIoT traffic. Here’s how:
- Identify Required Ports: Check the RemoteIoT documentation to find out which ports it uses.
- Add Rules: Log in to your firewall and add rules to allow traffic on those specific ports.
- Test the Connection: Once the rules are in place, test the connection to ensure it’s working.
Method 2: Use a Proxy Server
Another option is to use a proxy server to route your RemoteIoT traffic. Proxy servers act as intermediaries, allowing you to bypass firewall restrictions. Just make sure to choose a trusted proxy provider.
The Role of Port Forwarding
Port forwarding is another effective way to bypass firewall restrictions. Here’s how it works:
When you set up port forwarding on your router, you’re essentially telling it to forward incoming traffic on specific ports to a particular device on your network. This allows RemoteIoT to establish a connection even when you’re behind a firewall.
To set up port forwarding:
- Access Your Router: Log in to your router’s admin panel.
- Find the Port Forwarding Section: Look for the port forwarding or virtual server settings.
- Set Up Rules: Create rules to forward the required ports to your Mac’s IP address.
- Save and Test: Save the changes and test the connection to ensure everything is working.
Using VPNs to Access RemoteIoT
VPNs (Virtual Private Networks) are another great way to bypass firewall restrictions. By encrypting your traffic and routing it through a secure server, VPNs allow you to access RemoteIoT as if you were on the same network.
Here are some popular VPN options to consider:
- ExpressVPN: Known for its speed and reliability.
- NordVPN: Offers advanced security features like double encryption.
- CyberGhost: Great for beginners with a user-friendly interface.
Just remember to choose a reputable provider and configure the VPN properly to ensure seamless RemoteIoT access.
Ensuring Security While Bypassing Firewalls
While bypassing firewalls can be necessary, it’s important to prioritize security. Here are some tips to keep your data safe:
- Use Strong Passwords: Make sure your RemoteIoT account and devices are protected with strong, unique passwords.
- Enable Two-Factor Authentication: Add an extra layer of security by enabling 2FA on your account.
- Keep Software Updated: Regularly update RemoteIoT and your firewall to ensure you have the latest security patches.
- Monitor Activity: Keep an eye on your account activity and report any suspicious behavior immediately.
Common Issues and Troubleshooting Tips
Even with the best setup, issues can arise. Here are some common problems and how to fix them:
- Connection Timeout: Check your firewall rules and ensure the required ports are open.
- Device Not Recognized: Verify that your devices are properly connected to the network and added to RemoteIoT.
- Slow Performance: Optimize your network settings and consider using a faster internet connection.
- Security Alerts: Review your security settings and ensure everything is configured correctly.
If these solutions don’t work, don’t hesitate to reach out to RemoteIoT’s support team for further assistance.
Best Practices for Using RemoteIoT Behind a Firewall
To make the most of RemoteIoT behind a firewall, here are some best practices to follow:
- Plan Ahead: Understand your network setup and firewall configuration before attempting to use RemoteIoT.
- Document Your Setup: Keep detailed notes of your configuration to make troubleshooting easier in the future.
- Stay Updated: Regularly check for updates and improvements to both RemoteIoT and your firewall software.
- Test Regularly: Periodically test your connection to ensure everything is working as expected.
By following these practices, you’ll be well on your way to mastering RemoteIoT behind a firewall.
Wrapping It All Up
And there you have it—a comprehensive guide on how to use RemoteIoT behind a firewall on your Mac. From understanding the basics to overcoming common challenges, we’ve covered everything you need to know. Remember, while firewalls can be a hurdle, they’re also an essential part of your network security. By following the tips and tricks outlined in this article, you can enjoy the full benefits of RemoteIoT without compromising your safety.
Now, it’s your turn! If you found this article helpful, feel free to share it with your friends and colleagues. And if you have any questions or feedback, drop a comment below. We’d love to hear from you!
Until next time, stay connected and keep exploring the world of IoT. Happy managing!