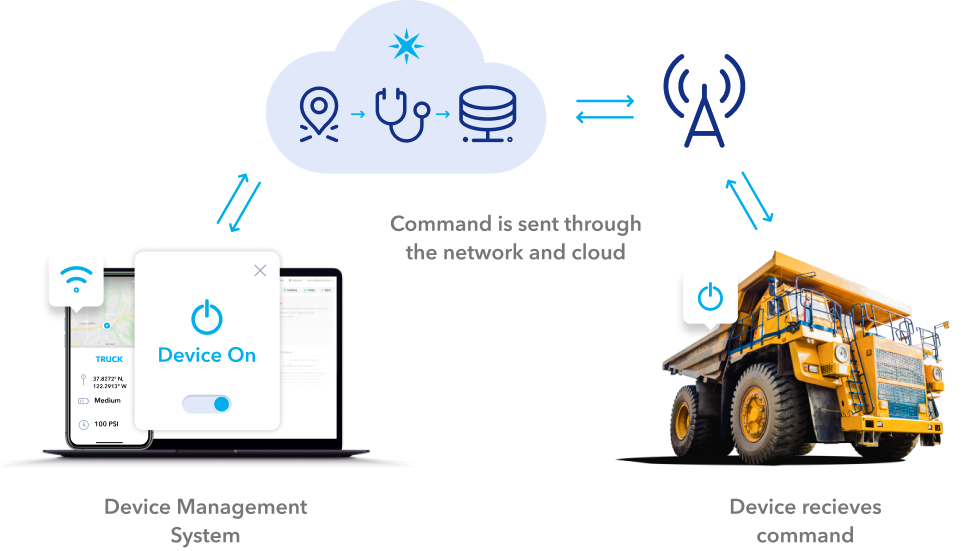
Secure Remote Control IoT Device Free: Your Ultimate Guide To Safety And Efficiency
Imagine this: you're chilling at the beach, sipping on a cold drink, while your smart thermostat back home adjusts the temperature automatically. Sounds awesome, right? But wait—how secure is your IoT device when you're controlling it remotely for free? Today, we're diving deep into the world of secure remote control IoT devices, exploring how you can protect yourself without breaking the bank. Whether you're a tech enthusiast or just someone trying to stay safe online, this guide is for you.
IoT devices are everywhere these days, from smart thermostats to security cameras. They make life easier, but they also come with risks. The good news? You don't have to spend a fortune to keep your devices secure. In this article, we'll walk you through the ins and outs of securing your IoT devices for free, ensuring peace of mind without compromising functionality.
We'll cover everything from setting up strong passwords to using free tools that boost security. So grab your favorite snack, and let's dive into the nitty-gritty of secure remote control IoT device management. Your future self will thank you!
Read also:Mydesinet Your Ultimate Guide To Indian Fashion And Beyond
Table of Contents:
- Introduction to Secure Remote Control IoT Device Free
- Understanding IoT Devices and Their Vulnerabilities
- Best Practices for Securing Your IoT Devices
- Free Tools for Enhancing IoT Security
- Why Strong Passwords Matter
- Securing Your Home Network
- Safe Remote Access Techniques
- Protecting Your Data with Encryption
- Common Mistakes to Avoid
- Future Trends in IoT Security
- Conclusion: Taking Control of Your IoT Security
Introduction to Secure Remote Control IoT Device Free
Secure remote control of IoT devices is no longer a luxury; it's a necessity. With more and more people relying on connected devices, the need for robust security measures has never been greater. But why should you pay for something you can do for free? By following a few simple steps, you can ensure your IoT devices are as secure as possible without spending a dime.
In this section, we'll explore the basics of IoT security and why it matters. We'll also touch on the importance of free solutions in today's tech-driven world. Let's get started!
Understanding IoT Devices and Their Vulnerabilities
IoT stands for "Internet of Things," and it refers to the network of physical objects embedded with sensors, software, and connectivity. These devices range from smart fridges to wearable fitness trackers. While they offer convenience, they also introduce potential vulnerabilities.
Key Vulnerabilities of IoT Devices
Here are some common vulnerabilities to watch out for:
- Weak default passwords
- Inadequate firmware updates
- Lack of encryption
- Unsecured network connections
By understanding these vulnerabilities, you can take proactive steps to secure your IoT devices. It's all about staying one step ahead of potential threats.
Read also:Ms Sethi Mms A Comprehensive Guide To Her Journey Achievements And Legacy
Best Practices for Securing Your IoT Devices
Securing your IoT devices doesn't have to be complicated. Here are some best practices to keep your devices safe:
First things first—always change the default passwords. It's shocking how many people overlook this simple step. Next, ensure your devices are updated regularly. Manufacturers often release patches to fix known vulnerabilities, so staying up-to-date is crucial.
Additional Tips
- Disable unused features
- Limit access to trusted devices
- Regularly monitor device activity
These practices might seem basic, but they form the foundation of a strong security strategy. Remember, security is a journey, not a destination.
Free Tools for Enhancing IoT Security
Who says security has to cost money? There are plenty of free tools available to help you secure your IoT devices. Here are a few worth checking out:
1. Wireshark
Wireshark is a powerful network protocol analyzer that lets you inspect network traffic. It's great for identifying suspicious activity on your network.
2. Nmap
Nmap is a network scanning tool that helps you discover devices on your network. It's perfect for ensuring no unauthorized devices are lurking around.
These tools might sound intimidating, but they're surprisingly easy to use once you get the hang of them. Plus, they're free, so you've got nothing to lose!
Why Strong Passwords Matter
Let's talk about passwords. Weak passwords are one of the biggest security risks out there. Think about it—if someone guesses your password, they could gain access to all your IoT devices. Scary, right?
So, what makes a strong password? Here are a few tips:
- Use a mix of uppercase and lowercase letters
- Include numbers and special characters
- Avoid using personal information
- Make it at least 12 characters long
Remember, the goal is to make your password as hard to guess as possible. And don't forget—never reuse passwords across multiple accounts!
Securing Your Home Network
Your home network is the backbone of your IoT ecosystem. If it's not secure, neither are your devices. Here's how you can fortify your network:
Start by changing your router's default settings. This includes the admin password and network name. Next, enable WPA3 encryption if your router supports it. It's the latest and most secure encryption standard available.
Other Network Security Tips
- Create a guest network for visitors
- Regularly update your router's firmware
- Use MAC address filtering to control access
By securing your home network, you're adding an extra layer of protection to your IoT devices. It's like locking the front door to your digital home.
Safe Remote Access Techniques
Remote access is one of the coolest features of IoT devices, but it also comes with risks. Here's how you can access your devices safely from anywhere:
First, consider using a Virtual Private Network (VPN). A VPN encrypts your internet connection, making it much harder for hackers to intercept your data. There are plenty of free VPN options available, so do some research to find the one that suits you best.
Alternative Solutions
- Use SSH tunnels for secure communication
- Set up port forwarding carefully
- Enable two-factor authentication wherever possible
These techniques might sound technical, but they're essential for keeping your remote access secure. Trust us—it's worth the effort!
Protecting Your Data with Encryption
Data encryption is another critical aspect of IoT security. Encryption scrambles your data so that only authorized parties can read it. Here's how you can implement encryption for your IoT devices:
Start by enabling encryption on your devices if it's available. Most modern IoT devices offer some form of encryption, so take advantage of it. Next, consider using encrypted storage solutions for sensitive data.
Encryption Tools to Explore
- BitLocker for Windows users
- FileVault for macOS users
- Veracrypt for cross-platform encryption
Encryption might seem like overkill, but it's one of the most effective ways to protect your data. Plus, it's free!
Common Mistakes to Avoid
Even the best-laid plans can go awry if you make common mistakes. Here are a few to watch out for:
- Ignoring firmware updates
- Using weak or reused passwords
- Failing to secure your network
- Not monitoring device activity
Avoiding these mistakes is half the battle when it comes to IoT security. Stay vigilant, and you'll be ahead of the curve.
Future Trends in IoT Security
As IoT technology continues to evolve, so do the security challenges. Here's what you can expect in the near future:
First, expect more emphasis on AI-driven security solutions. AI can analyze patterns and detect anomalies in real-time, making it a powerful ally in the fight against cyber threats. Second, quantum encryption might become a reality, offering unparalleled security for your data.
Staying Ahead of the Curve
- Keep up with the latest security trends
- Invest in devices with built-in security features
- Regularly educate yourself on best practices
The future of IoT security is bright, but it requires effort and commitment. Stay informed, and you'll be ready for whatever comes your way.
Conclusion: Taking Control of Your IoT Security
In conclusion, securing your IoT devices doesn't have to be a daunting task. By following the tips and best practices outlined in this article, you can protect your devices without spending a fortune. Remember, security is about being proactive and staying informed.
We encourage you to take action today. Change those default passwords, update your firmware, and explore the free tools available. And don't forget to share this article with your friends and family. The more people know about IoT security, the safer we all are.
So, what are you waiting for? Take control of your IoT security and enjoy the peace of mind that comes with it. Your future self will thank you!