Mastering RemoteIoT SSH AWS: Your Ultimate Guide To Secure Cloud Connections
Alright, listen up, folks. If you're diving into the world of IoT (Internet of Things) and cloud computing, there's one thing you absolutely need to wrap your head around: remoteIoT SSH AWS. This isn't just some buzzword—it's the backbone of secure communication between your IoT devices and Amazon Web Services (AWS). Imagine having a super-secure tunnel that lets your devices talk to each other without any pesky hackers eavesdropping. Yeah, that’s what we’re building here. So, buckle up because we’re about to deep-dive into the nitty-gritty of this tech marvel.
You see, in today’s digital jungle, security is king. Whether you're managing smart home devices, industrial sensors, or even wearable tech, the last thing you want is someone snooping around your data. That's where SSH (Secure Shell) comes in. It’s like a digital bouncer, making sure only authorized guests get access to the VIP lounge—your cloud servers. But let's not get ahead of ourselves. First, we need to understand the basics.
Now, if you're wondering why AWS is such a big deal in this equation, here's the scoop. AWS is like the Tesla of cloud services. It’s fast, reliable, and packed with features that make managing IoT devices a breeze. Combine that with SSH, and you’ve got yourself a winning combo. So, whether you're a tech-savvy pro or just starting out, this guide is here to walk you through everything you need to know about remoteIoT SSH AWS. Let's get started!
Read also:Muhammad Ali Jr Boxing The Legacy Continues
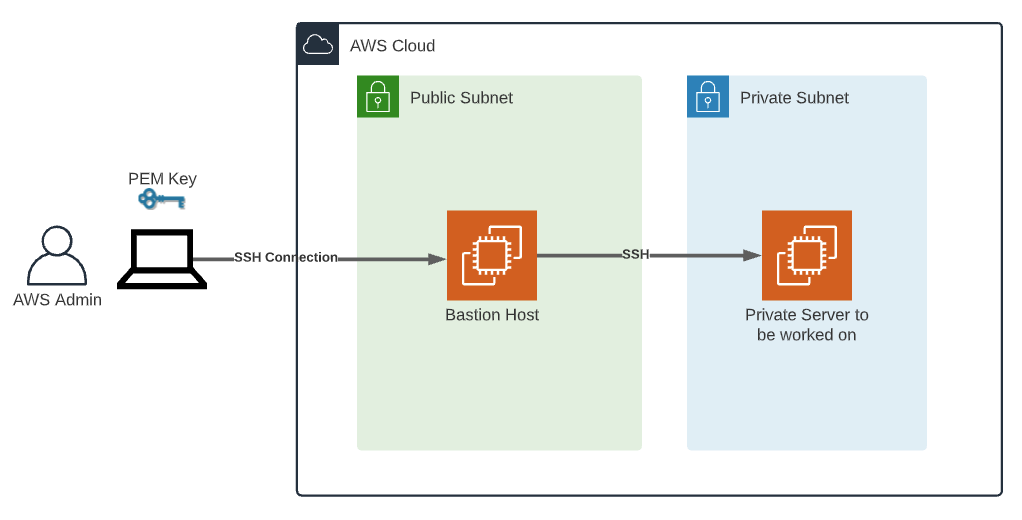
What is RemoteIoT SSH AWS Anyway?
Let’s break it down. RemoteIoT SSH AWS is basically the process of creating a secure connection between your IoT devices and AWS servers using SSH. Think of it as a secret handshake that only your devices and AWS can understand. This handshake ensures that all communication is encrypted, protecting your data from prying eyes. Pretty cool, right?
Why SSH is the Go-To Protocol
SSH isn't just any protocol; it's the gold standard when it comes to secure communication. Here are a few reasons why:
- Encryption: SSH encrypts all data transmitted between devices, making it nearly impossible for hackers to intercept.
- Authentication: It uses public-key cryptography to verify the identity of devices, ensuring only authorized ones can connect.
- Flexibility: SSH supports a wide range of applications, from file transfers to remote command execution.
So, whether you're sending sensitive data or just checking the status of your devices, SSH has got your back.
Understanding AWS in the IoT Ecosystem
AWS isn’t just a cloud provider; it’s a powerhouse. With its IoT Core service, AWS makes it ridiculously easy to connect, monitor, and manage your IoT devices at scale. But what makes AWS stand out in the world of IoT?
Scalability: The Key to Success
One of the biggest advantages of AWS is its scalability. Whether you're managing a handful of devices or thousands of them, AWS can handle it all without breaking a sweat. This means you can start small and grow your IoT infrastructure as needed, without worrying about running out of resources.
Setting Up RemoteIoT SSH AWS: Step by Step
Alright, now that we’ve covered the basics, let’s dive into the setup process. Setting up remoteIoT SSH AWS might sound intimidating, but trust me, it’s easier than you think.
Read also:Face Tattoo Justin Bieber The Bold Move That Sparked A Revolution
Step 1: Install SSH on Your Device
First things first, you need to install SSH on your IoT device. Most Linux-based devices come with SSH pre-installed, but if not, you can easily install it using a package manager like apt or yum. For example, on a Raspberry Pi, you can install SSH by running:
sudo apt-get update && sudo apt-get install openssh-server
Step 2: Create SSH Keys
Next, you’ll need to create SSH keys. These keys are like digital IDs that allow your device to authenticate itself with AWS. To create a key pair, run the following command:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"
This will generate a public and private key. Keep the private key safe—it’s like the password to your device.
Step 3: Configure AWS Security Groups
Now it’s time to configure AWS security groups. Think of security groups as firewalls that control inbound and outbound traffic to your AWS instances. To allow SSH access, you’ll need to add a rule that permits traffic on port 22 (the default SSH port).
Best Practices for Secure RemoteIoT SSH AWS Connections
Security is paramount when it comes to IoT and cloud computing. Here are some best practices to keep your connections safe:
- Use strong, unique passwords for your SSH keys.
- Disable password authentication and rely solely on key-based authentication.
- Regularly update your devices and AWS instances to patch any security vulnerabilities.
- Monitor your connections for any suspicious activity.
Common Challenges and How to Overcome Them
Let’s face it, setting up remoteIoT SSH AWS isn’t always smooth sailing. Here are some common challenges you might encounter and how to overcome them:
Challenge 1: Connectivity Issues
Solution: Check your network settings and ensure that your device can reach the AWS servers. Also, verify that your security groups are configured correctly.
Challenge 2: Key Authentication Failures
Solution: Double-check your SSH keys and make sure they match. Also, ensure that the correct permissions are set on your private key file.
Real-World Applications of RemoteIoT SSH AWS
So, how is remoteIoT SSH AWS being used in the real world? Here are a few examples:
Smart Agriculture
Farmers are using IoT sensors to monitor soil moisture, temperature, and other environmental factors. These sensors send data to AWS via SSH, allowing farmers to make data-driven decisions to optimize crop yields.
Industrial Automation
Manufacturing plants are leveraging IoT devices to monitor machinery performance and predict maintenance needs. By securely connecting these devices to AWS, plant managers can reduce downtime and improve efficiency.
Future Trends in IoT and Cloud Computing
The future of IoT and cloud computing looks promising. With advancements in AI and machine learning, we can expect even more sophisticated applications of remoteIoT SSH AWS. For example, imagine AI-powered IoT devices that can not only monitor but also predict and respond to changes in their environment. That’s the future we’re heading towards.
Resources and Further Reading
Here are some resources to help you dive deeper into remoteIoT SSH AWS:
Conclusion: Take Your IoT Game to the Next Level
There you have it, folks. RemoteIoT SSH AWS is your ticket to secure, scalable IoT solutions. By following the steps outlined in this guide, you can set up a secure connection between your devices and AWS in no time. Remember, security is key, so always follow best practices to protect your data.
Now, here’s the fun part. I want you to take action. Whether it’s setting up SSH on your device, configuring AWS security groups, or exploring real-world applications, don’t just sit there—get your hands dirty. And don’t forget to share your experiences in the comments below. Who knows, you might just inspire someone else to take the leap into the world of IoT and cloud computing.
Until next time, stay curious and keep learning!
Table of Contents
- What is RemoteIoT SSH AWS Anyway?
- Why SSH is the Go-To Protocol
- Understanding AWS in the IoT Ecosystem
- Setting Up RemoteIoT SSH AWS: Step by Step
- Best Practices for Secure RemoteIoT SSH AWS Connections
- Common Challenges and How to Overcome Them
- Real-World Applications of RemoteIoT SSH AWS
- Future Trends in IoT and Cloud Computing
- Resources and Further Reading
- Conclusion