Unlock The Power Of RemoteIoT Platform SSH Key For Seamless Connectivity
Hey there tech enthusiasts! Ever wondered how you can securely connect to your IoT devices from anywhere in the world? Well, buckle up because we're diving deep into the world of RemoteIoT platform SSH key. This is your ultimate guide to understanding, implementing, and mastering the art of secure remote access for IoT devices. Whether you're a beginner or a seasoned pro, this article has got you covered.
Let’s face it, IoT is not just a buzzword anymore; it's the backbone of modern technology. From smart homes to industrial automation, IoT devices are everywhere. But what happens when you need to access these devices remotely? That's where RemoteIoT platform SSH key comes into play. It's like having a virtual key to unlock your devices no matter where you are.
Now, before we dive deeper, let me assure you that this isn't just another tech jargon-filled article. We’re going to break it down into simple terms, share practical tips, and even throw in some real-world examples. So, grab a coffee and let’s get started!
Read also:Serenity Cox The Rising Star Shining Bright In The Entertainment World
What Exactly is RemoteIoT Platform SSH Key?
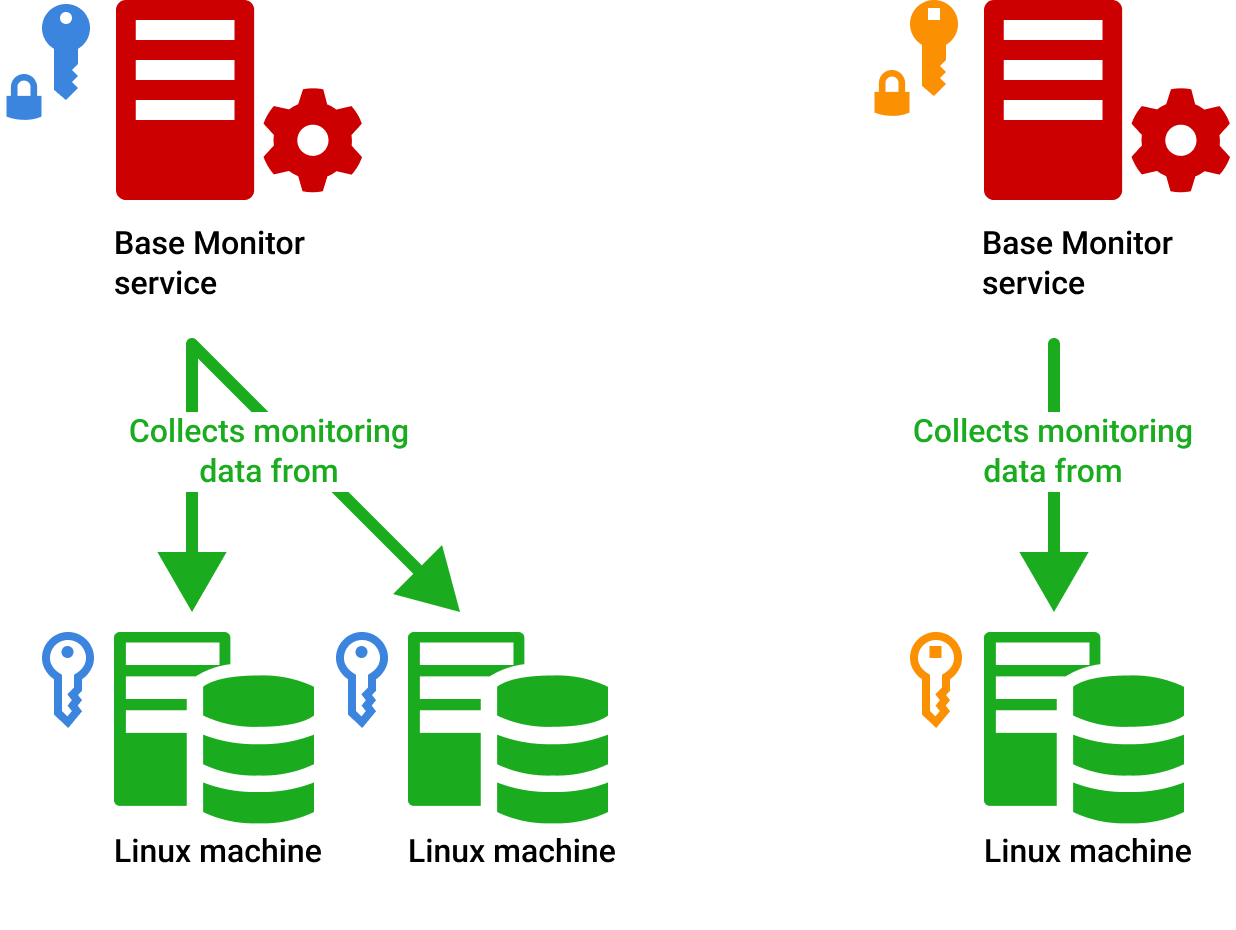
Alright, let’s start with the basics. RemoteIoT platform SSH key is essentially a cryptographic key used to establish a secure connection between your device and the RemoteIoT platform. Think of it as a digital handshake that ensures only authorized users can access your IoT devices. This key is crucial for maintaining security and preventing unauthorized access.
SSH stands for Secure Shell, and it’s a protocol that provides a secure way to access a remote computer or device. The RemoteIoT platform leverages this protocol to allow users to manage their IoT devices remotely without compromising on security.
Why is RemoteIoT Platform SSH Key Important?
In today’s interconnected world, security is paramount. Imagine leaving your front door unlocked or giving out your house keys to strangers. That’s exactly what happens when you don’t secure your IoT devices properly. A RemoteIoT platform SSH key acts as your digital lock and key, ensuring that only trusted individuals can access your devices.
Here’s why it’s important:
- Enhanced Security: Prevent unauthorized access by using strong encryption.
- Remote Access: Manage your IoT devices from anywhere in the world.
- Peace of Mind: Rest assured knowing your devices are protected.
- Scalability: Easily manage multiple devices with a single key.
How Does RemoteIoT Platform SSH Key Work?
Now that we understand the importance of SSH keys, let’s talk about how they actually work. When you set up a RemoteIoT platform SSH key, you’re essentially creating a pair of keys – a public key and a private key. The public key is shared with the RemoteIoT platform, while the private key remains securely on your device.
Here’s a quick breakdown of the process:
Read also:Steve Dulcich Children A Closer Look At Family Life Beyond The Spotlight
- The RemoteIoT platform generates a public key and sends it to your device.
- Your device stores the private key and uses it to authenticate with the platform.
- Once authenticated, you can securely access and manage your IoT devices.
Setting Up Your RemoteIoT Platform SSH Key
Setting up an SSH key might sound intimidating, but trust me, it’s easier than you think. Follow these simple steps to get started:
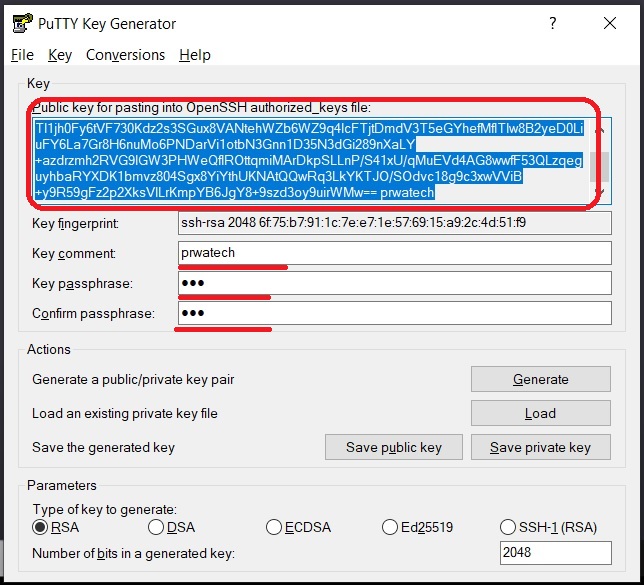
Step 1: Generate Your SSH Key
The first step is to generate your SSH key pair. You can do this using tools like OpenSSH or PuTTY. Here’s how:
- Open your terminal or command prompt.
- Type the command: ssh-keygen -t rsa -b 4096
- Follow the prompts to create your key pair.
Step 2: Add the Public Key to RemoteIoT Platform
Once you’ve generated your key pair, it’s time to add the public key to the RemoteIoT platform. This can usually be done through the platform’s settings or configuration page.
Step 3: Test Your Connection
After adding your public key, it’s a good idea to test your connection. Try accessing your IoT device remotely to ensure everything is working as expected.
Best Practices for Using RemoteIoT Platform SSH Key
Now that you know how to set up an SSH key, let’s talk about some best practices to keep your devices secure:
- Use Strong Passwords: Even with an SSH key, it’s important to use strong passwords for added security.
- Regularly Update Keys: Don’t use the same key forever. Regularly update your keys to minimize the risk of compromise.
- Limit Access: Only grant access to trusted users and devices.
- Monitor Activity: Keep an eye on who’s accessing your devices and when.
Common Challenges with RemoteIoT Platform SSH Key
While SSH keys are incredibly useful, they’re not without their challenges. Here are some common issues you might face and how to overcome them:
Challenge 1: Key Management
Managing multiple keys can be a hassle. To overcome this, consider using a key management system or tool to keep everything organized.
Challenge 2: Key Expiration
SSH keys don’t last forever. Make sure to set up a reminder system to renew your keys before they expire.
Challenge 3: Security Breaches
Even with SSH keys, security breaches can still happen. Regularly update your software and firmware to patch any vulnerabilities.
Real-World Applications of RemoteIoT Platform SSH Key
Let’s take a look at some real-world examples of how RemoteIoT platform SSH key is being used:
Application 1: Smart Homes
Imagine being able to control your smart home devices from anywhere in the world. With a RemoteIoT platform SSH key, you can securely access and manage your smart home system no matter where you are.
Application 2: Industrial Automation
In the world of industrial automation, secure remote access is crucial. SSH keys allow engineers to monitor and control machines remotely, reducing downtime and increasing efficiency.
Future Trends in RemoteIoT Platform SSH Key
As technology continues to evolve, so does the world of SSH keys. Here are some trends to watch out for:
- Quantum Computing: The rise of quantum computing could render traditional encryption methods obsolete. Expect new advancements in SSH key technology to combat this threat.
- AI Integration: AI-powered key management systems could revolutionize how we handle SSH keys in the future.
- Blockchain: Blockchain technology could provide a more secure and decentralized way to manage SSH keys.
Data and Statistics Supporting RemoteIoT Platform SSH Key
According to a recent study by Cybersecurity Ventures, cybercrime is expected to cost the world $10.5 trillion annually by 2025. This highlights the importance of securing your IoT devices with tools like RemoteIoT platform SSH key.
Another study by Gartner predicts that by 2023, over 75% of enterprises will have adopted IoT solutions, making secure remote access more important than ever.
Conclusion
And there you have it, folks! A comprehensive guide to RemoteIoT platform SSH key. From understanding the basics to exploring real-world applications and future trends, we’ve covered it all. Remember, securing your IoT devices is not just a luxury; it’s a necessity in today’s digital age.
So, what are you waiting for? Start implementing these tips and take your IoT security to the next level. Don’t forget to share this article with your friends and colleagues, and feel free to leave a comment below if you have any questions or feedback. Happy securing!
Table of Contents
- What Exactly is RemoteIoT Platform SSH Key?
- Why is RemoteIoT Platform SSH Key Important?
- How Does RemoteIoT Platform SSH Key Work?
- Setting Up Your RemoteIoT Platform SSH Key
- Best Practices for Using RemoteIoT Platform SSH Key
- Common Challenges with RemoteIoT Platform SSH Key
- Real-World Applications of RemoteIoT Platform SSH Key
- Future Trends in RemoteIoT Platform SSH Key
- Data and Statistics Supporting RemoteIoT Platform SSH Key
- Conclusion